Automatic Certificate Management Environment (ACME) with NetScaler using Ansible
Building on our previous guide, “Prep for 47-Day TLS Certificate,” this post dives deeper into empowering your NetScaler automation with Ansible and the ACME protocol. The goal: transform certificate management from a manual headache into a seamless, resilient process.
Why ACME for Certificate Automation?
The Automatic Certificate Management Environment (ACME) protocol is designed to eliminate manual drudgery in obtaining browser-trusted certificates, enabling fully automated, hands-off workflows. Originally developed by the Internet Security Research Group as the backbone of Let’s Encrypt, ACME is now a widely adopted industry standard, trusted by leading certificate authorities.
Securing a certificate with ACME requires proving domain ownership through one of two challenge types:
HTTP-01 challenge: Fulfill the challenge by serving a unique token over HTTP (port 80) at a specific path on the domain.
DNS-01 challenge: Publish a verification key as a DNS TXT record to satisfy the challenge request.
Automating NetScaler with Ansible
Ansible’s NetScaler collection equips teams to configure, manage, and orchestrate NetScaler ADC appliances efficiently and repeatably. This is achieved through purpose-built modules harnessing the NITRO API for streamlined automation.
Collection: Ansible Galaxy - netscaler.adc
Elevate Your Workflow with AWX
Ansible AWX delivers a robust, open-source interface and REST API layered atop Ansible, offering advanced features for secure collaboration. Leverage role-based access control, inventory management, job tracking, and scheduled automation to tighten governance and accelerate your team’s NetScaler initiatives.
Implementation:
AWX
In AWX create an inventory containing the groups and hosts, the Ansible playbook will run on all hosts. This is the location where variables are defined, example:
Next steps:
Create a project that, this is the link between the GIT location and AWX
Create a template linking the inventory, project and the playbook itself
Create a schedule to execute the playbook on a daily base
Ansible
From the main playbook include the acme task while looping the “certificates” list:
Using openssl the prerequisites to start a ACME challenge can be created:
Generate account key
Generate private key
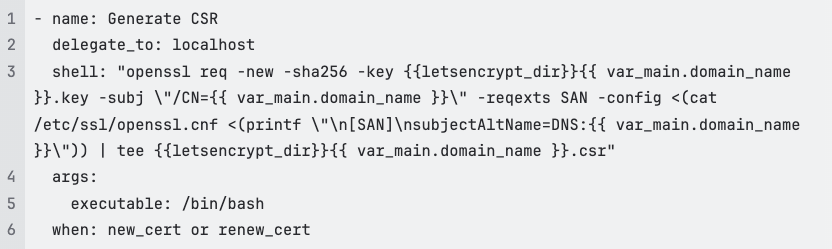
Generate CSR
Begin ACME challenge
The token to complete the challenge is now registered into the acme_challenge_your_domain variable. This variable will be used to create a responder on the NetScaler and link it to the CS virtual server.
Note:
It can be useful to create a user-defined audit message to get some logging in syslog
Complete ACME challenge to issue the certificate:
Note:
It’s important to unbind and remove the responder after the challenge has been validated
The server certificate is now available and can be installed on the NetScalers.
Note:
The private key is not password protect by default, a task should be implemented to password protect the private key
The ACME protocol will fetch a full chain certificate for you containing the CA-certificates. This can be used to install the CA’s on the NetScaler and make the links.
The Let’s Encrypt certificates are only valid for 90 days, the certificates can be automatically renewed before expiring.
Updating server certificate is not possible with the Ansible collection, a Nitro call was used to work around this:
Unlock Effortless Certificate Management
Ready to say goodbye to manual certificate renewals and streamline your security operations? By integrating Ansible, AWX, and ACME with NetScaler, it’s easier than ever to maintain airtight, up-to-date protection for your digital assets.
Have questions, or want to see how this approach fits your environment? Contact one of our experts directly for more information and advice.