Lock down your APIs at the Edge
Smarter security starts early: API token validation & schema enforcement at the edge
APIs are the backbone of modern digital infrastructure-connecting services, powering automation, and driving business innovation. But with this power comes risk: exposed endpoints and weak authentication can turn a single vulnerability into a costly breach. At Blubyte, we believe smarter security starts at the edge, long before a malicious request ever reaches your application.
In this article, we break down how NetScaler’s advanced features-API Token Validation and Schema Enforcement-help you secure your APIs proactively, without sacrificing speed or reliability.
Why edge security matters for apis
APIs are the heart of today’s applications, but they’re also a prime target for attackers. Traditional security models often rely on backend checks, which means your infrastructure is already spending resources before a threat is even detected. By moving security controls to the edge, you block bad actors before they can do any damage-saving time, resources, and reputation.
Step 1: validate API tokens at the edge the challenge:
Most organizations validate OAuth2 bearer tokens (from identity providers or API consumers) at the backend. This means your APIs are already parsing and processing requests-even those with invalid or expired tokens.
Blubyte’s solution:
With NetScaler, token validation happens at the edge. Invalid requests are rejected instantly, never touching your backend.
Key Benefits:
Inline validation of OAuth tokens (signature, expiry, claims)
Performance boost via token caching
Zero Trust alignment-no assumptions at the perimeter
Flexible integration with any identity provider
How it works:
NetScaler uses an OAuthAction to validate tokens, either locally or through token introspection with your IDP.
OAuthAction example
If the token is valid: the request continues.
If not: a 401 Unauthorized is returned-no backend hit.
Step 2: Enforce API Schema with Swagger/OpenAPI
The challenge:
Authentication alone isn’t enough. You need to ensure APIs are being used as intended, with the correct URLs, HTTP methods, and request structures.
The Blubyte Solution:
NetScaler imports your OpenAPI (Swagger) spec and uses it as a contract-whitelisting valid endpoints and blocking everything else.
Why this matters:
Whitelist only valid URLs and HTTP methods
Block unexpected or malicious requests
Keep DEV and OPS teams in sync (specs are often auto-generated from code)
How it works:
Import your API spec (e.g., myApp.json)-integrate this step into your Ansible or Terraform pipeline.
Create a validation policy using HTTP.REQ.API.
Bind a responder policy to reject anything outside the spec.
Example config:
Configuration example
Now, only endpoints and methods defined in your spec are allowed-everything else is dropped or redirected.
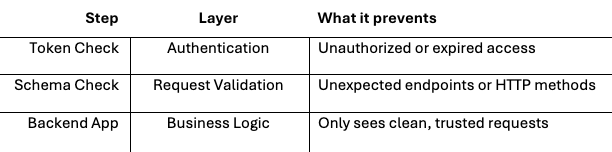
Defense in depth: combining token & schema validation
When you validate tokens and enforce schema, you build a multi-layered security stack:
Multi-layered security stack example
By handling these checks at the NetScaler level, you save backend resources, improve response times, and strengthen your security posture-all at once1.
Final Thoughts
APIs need to be open, fast, and reliable-but they also need to be secure. With NetScaler and Blubyte’s expertise, you don’t have to choose between performance and protection. Token validation, real-time traffic filtering, and schema enforcement happen transparently, with no code changes required.
Would you like to speak directly with a NetScaler expert, without intermediaries or delays? Contact us now for immediate expert assistance!